Your Secrets, Distributed.
Securely split sensitive data into self-contained HTML "parts." Losing one doesn't matter. Stealing one is useless. Only you and your threshold of parts can bring the secret back to life.
Project Context & Motivation
This project was motivated by the the Hacker News discussion "Horcrux: Split your file into encrypted fragments" and the desire to create a more self contained and practical implementation of the same concept for personal use.
The goal was for this tool to work on any platform and require no dependencies (other than a web browser), and be future-proof enough to be usable decades from now. An excellent similar tool was created by Ian Coleman (https://iancoleman.io/shamir/) which heavily inspired this project, this iteration adds more features such as self-contained parts and optional password protection.
How to Use
The entire process executes locally within your browser's memory.
Input Locally
Paste your secret (text, seed phrase, password) into the browser. It never leaves your device.
Set Thresholds
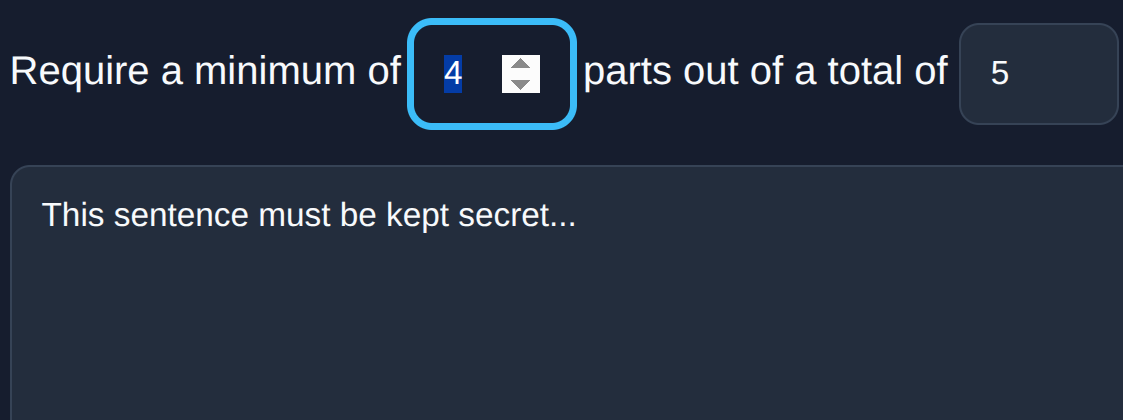
Define the total number of parts and the minimum required to recover. E.g., "3 of 5".
Download & Scatter
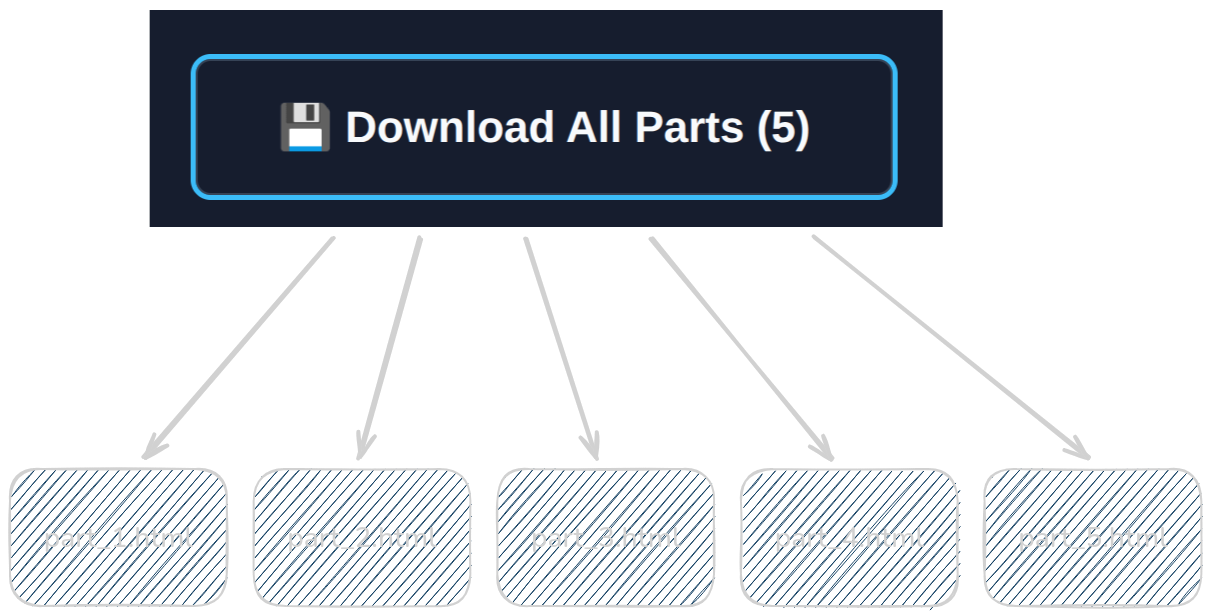
Get individual HTML files. Store them on USBs, different cloud services, or share them with trusted contacts.
Reassemble Anywhere
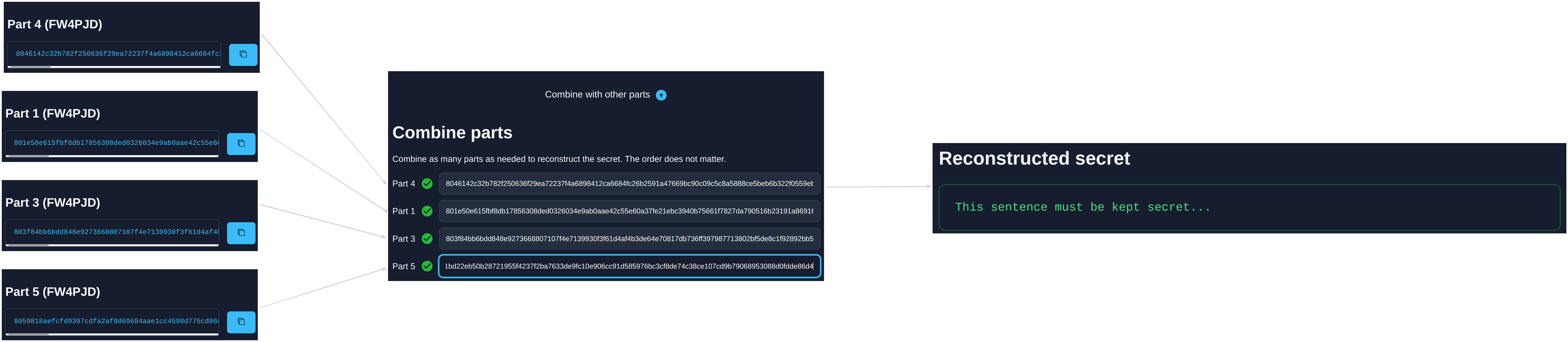
Open any single part file in a browser. Paste in the remaining required parts to unlock the secret.
01. The Algorithm
This tool utilizes Shamir's Secret Sharing to split data into unique parts. This algorithm provides Information-Theoretic Security, meaning that even with infinite computing power, an attacker with fewer than the required parts can never reconstruct the secret.
The core logic is based on the proven, open-source secrets.js implementation, which was security audited in 2019.
02. Fully self-contained
All the "parts" generated by the split tool are fully self-contained HTML files with an embedded combiner tool and work fully offline*.
This means that to recover a secret, all you will ever need is a standard web browser and the required parts. The combiner tool only uses standard JavaScript, the DOM API as well as the Web Crypto API, which provides long term compatibility and make the parts future-proof**.
* NOTE: The combiner tool can also be used a as fully offline, self-contained tool by simply saving the HTML page.
** In the very unlikely event that a self-contained part becomes incompatible or doesn't work, an independent combiner tool written in a different programming language (Python) is available in the GitHub Repository to recover the secret.
Practical Applications
Digital Inheritance
Distribute shares of your master password to family members. No one can access your accounts alone, but they can recover access together if you are incapacitated.
Geographic Redundancy
Split your primary email recovery code. Store shares in different physical locations (home, office, safe) to ensure a single fire or burglary doesn't lock you out.
Collaborative Custody
Protect sensitive family documents by requiring a "quorum" of trusted friends to unlock them. This ensures that no single person holds the power of access.